The Privacy & Security Nightmare That Is Mobile
by Lindsay Rowntree on 14th Jan 2019 in News

In his latest piece, exclusively for ExchangeWire, Dr Augustine Fou, cybersecurity and ad fraud researcher, explains the many reasons that mobile is such a cybersecurity headache that continues to fly under the radar.
I woke up in a cold sweat, my mind racing with a litany of unimaginable horrors brought on by today’s mobile technology and apps. Combine that with the collection and abuse of personal information by ad tech, and we have the perfect storm for a privacy and security nightmare that most people are not even aware of yet.
As a cybersecurity researcher, I have seen these attacks in real life already. The only question is when, not if, these attacks are observed and documented by others and publicly acknowledged. What follows is not a research paper with data, but hopefully a wake up call to other researchers, marketing practitioners, and even consumers, to keep an eye out for the various attacks that compromise security and privacy.
Keyboard apps
What if the keyboard apps that you voluntarily downloaded, installed, and gave permissions to, were logging everything you type, including usernames and passwords? They actually do, and you gave them explicit permission to send data back to their servers, supposedly to help them improve the service. Don’t think this is happening? Remember those celebrity Instagram account takeovers? Those were not sophisticated hacks. Instead, the celebrities and millennials that use Instagram are the very ones who also use third-party keyboard apps – so they have effectively just given the hackers their Instagram logins, unknowingly. And the keyboard apps also see the URLs you type in when browsing – including the porn sites, dating sites, and everything else in between. Would you be embarrassed if they threatened to release that to the public?
Use the keyboard app built into your phone.
Camera apps
What if the camera apps that you downloaded to make cute and silly faces were saving your selfie face pictures and sending them to the 'mothership' (their servers)? Users choose the best shots and apply cute puppy eyes, nose, mouth, and ears for fun. But, unbeknownst to them, they are voluntarily sharing many accurate headshots of themselves, which can later be used to face-unlock phones. Don’t think this is possible? Consider that most phones don’t have or use an infrared depth-sensing camera to verify faces, like the latest Apple iPhones. And it has shown that Android facial recognition has already been fooled. And don’t forget, camera apps have access to all your nude selfies and permission to send stuff back to their servers.
Use the camera app built into your phone.
Flashlight apps
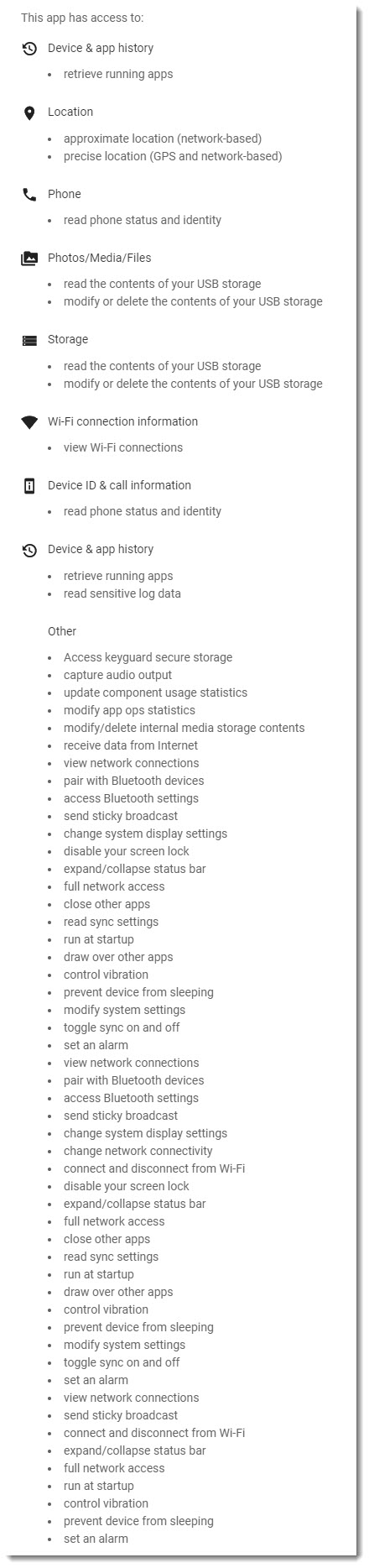
What if the flashlight apps that you installed ran in the background 24/7, even if you never opened it to use (since you have built-in flashlight functionality on your phone). Flashlight apps have been documented to ask for way too many permissions than is logical (see graphic) and they abuse those permissions to do bad things, too many to name. But they have loaded ads in the background, loaded webpages in the background, clicked on things, attempted to subscribe to services the user never intended to, and even attempted to make purchases using forms of payment already associated with the mobile device.
Use the flashlight functionality that came with your phone.
Gaming apps
What if the gaming apps that your kids installed are using their repeated clicks to click on hidden ads? What if they are also recording the location, gyroscope, and accelerometer data as the person plays the game? This human-interaction data can be easily replayed to defeat fraud-detection tech that is looking for human-like or nonhuman interactions with the mobile device. Do you still think your mobile fraud detection works now? And, in addition to simple ad fraud (loading ad impressions in the background) malicious gaming apps can even make small in-game purchases from themselves, using whatever form of payment the user has stored in the device, and even given it permission to perform – 'in-game purchases' permission. And by the way, they can also subscribe to premium porn sites or pay for live nudie-cam streams for you.
Monitor and restrict kids’ ability to download apps. You should be there when they do and check what permissions you are giving to the app. If you see anything strange, deny permission and uninstall right away.
SMS apps
What if an app you downloaded to do chat, SMS, and other communications, listened for your two-factor authentication codes and intercepted them to log into your bank accounts, PayPal, or anything else you thought was protected by 2FA? After all, you gave it permission to read and delete, send and receive SMS messages – they didn’t say you had to know when they did that. And they likely have permission to access and turn on the microphone and camera on the mobile device. These apps are listening in on every conversation and sending snippets or everything back to some server somewhere. And remember the story about Baidu’s 'Deep Voice' AI being able to clone anyone’s voice in 3.7 seconds, using sample snippets? Do you think your online banking that verifies it’s you by using your voice is still secure?
Use the chat and messaging apps built into the phone.
Anti-malware apps
What if the anti-malware, anti-virus, cleaner, and optimisation apps you installed on your mobile device, and gave admin privileges to, were actually the malware itself? Yeah, true story. See for yourself 'Avast is malware'. Those admin privileges mean they can look at the other apps installed or running on your device, they can download and install new ones, they can hide apps from normal view, and even create invisible app icons so you don’t even know they are there. Ever notice that your phone keeps running hot, or your battery is gone before lunchtime, or your monthly bandwidth gets used up by the third day of the month?
Just avoid downloading bad apps in the first place, then you won’t need an anti-malware app.
Still don’t think the above is possible or happening already? Remember those Samsung and Vizio smart TVs that were listening in on all conversations and sending data back to their servers? Remember those Lenovo laptops with built-in, and uninstallable, spyware and HP laptops with hidden keyloggers? Remember those low-cost Blu and TCL Android phones that had built in malware that sent telemetry back to servers in China? More examples can be found here.
Wait, was I in fact sleeping? Or was I awake all along? Are you all in this nightmare too?
Ad FraudCybersecurityIn-AppIn-App FraudMobile








Follow ExchangeWire