'Sambreel is Still Injecting Ads. Video Advertisers, Beware', by Douglas de Jager, CEO spider.io
by Romany Reagan on 14th Aug 2013 in News

Background: Sambreel’s AdWare was Ostensibly Shut Down Last Year.
On December 9, 2011, the Wall Street Journal called Sambreel out for illegitimately injecting ads into Facebook and Google webpages via adware browser plugins like PageRage and BuzzDock.
Facebook subsequently blocked its users from using Sambreel’s adware browser plugins whilst accessing Facebook webpages. Sambreel responded by suing Facebook, claiming violations of Sections 1 and 2 of the Sherman Antitrust Act. The case was thrown out of court.
With Sambreel’s adware publicly exposed, major sell-side platforms and ad exchanges like PubMatic, Rubicon Project, and OpenX dropped Sambreel as a supplier of display ad inventory in 2012.
Sambreel is Alive and Kicking.
Sambreel has two more plugins, Easy YouTube Video Downloader plugin and Best Video Downloader. These plugins are part of a software browser tool suite provided by Yontoo and Alactro. Yontoo and Alactro have been identified as subsidiaries of Sambreel.
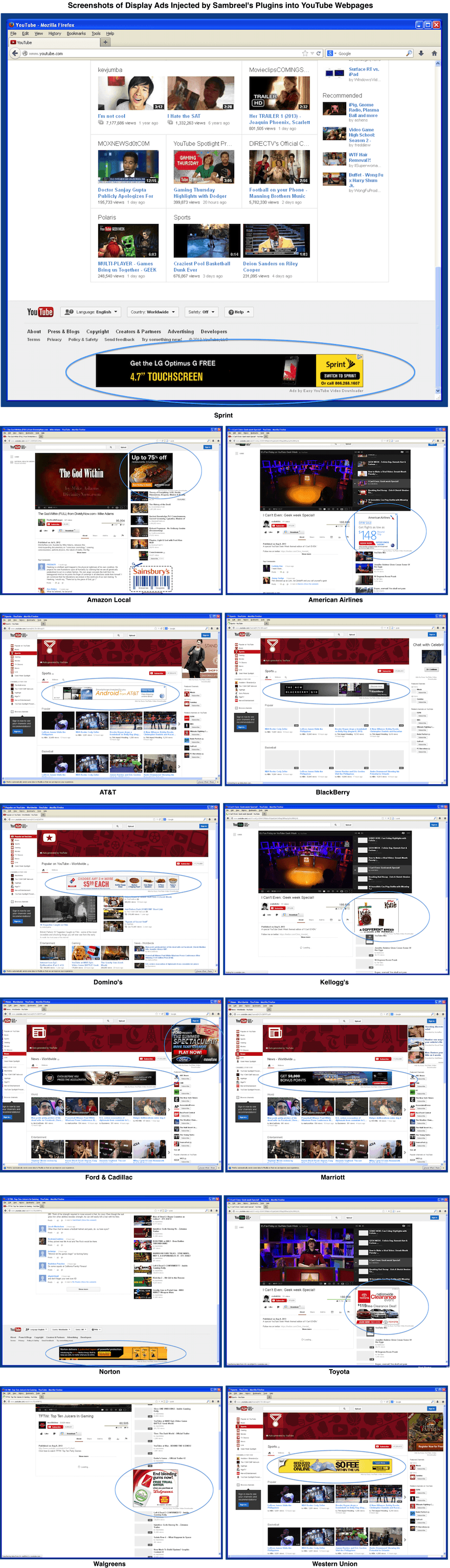
When a user who has installed these plugins visits YouTube, multiple display ad slots are injected across the YouTube homepage, channel pages, video pages and search results pages. These display ad slots are being bought today by premium advertisers like Amazon Local, American Airlines, AT&T, BlackBerry, Cadillac, Domino’s, Ford, Kellogg’s, Marriott, Norton, Toyota, Sprint, Walgreens and Western Union. Screenshots are shown below.
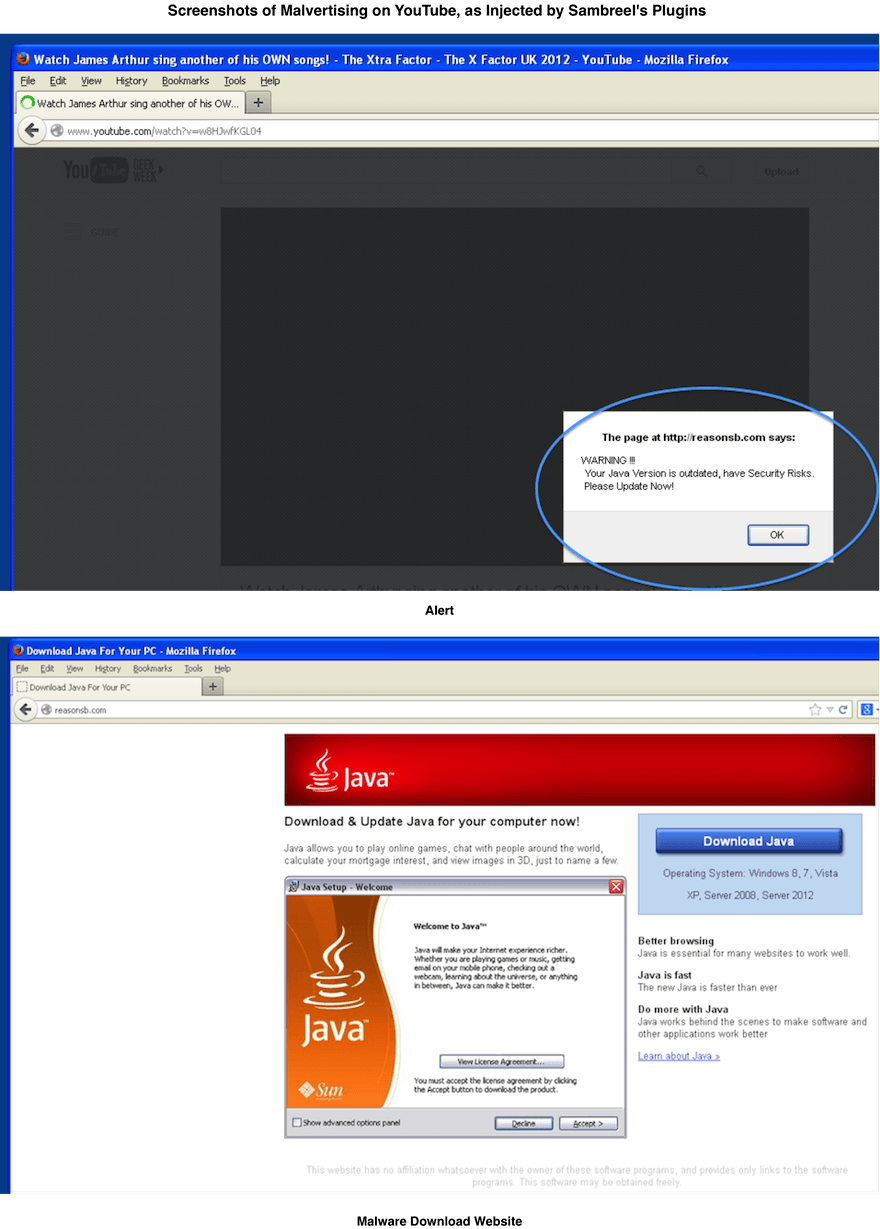
The display ad slots injected by Sambreel are also being bought today by malvertisers—advertisers who provide malicious or malware-laden advertisements with a view to spreading malware to new users. Example screenshots are included below. The first screenshot shows a fake alert, which suggests to the user that a Java update is required. If the user clicks the OK button, then the user is taken to the disreputable site shown in the second screenshot.
This sort of malvertising would be unlikely to impact YouTube users without Sambreel’s involvement. Google has strict ad-quality processes, and Sambreel’s plugins bypass these.
How are the Ads Injected?
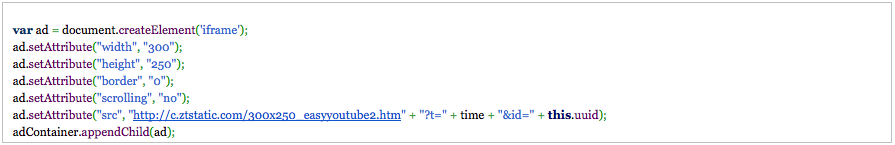
Sambreel’s plugins inject ads by adding iframe elements to the page, hosted on the c.ztstatic.com domain:
From within these iframes, the available ad slot is passed on to AdMatter. AdMatter describes itself as a “targeted ad cloud”. The AdMatter homepage is titled Sambreel and contains no content. This has been the case since October 2012, which is when Sambreel was reported as having been blocked by the sell-side platforms and the ad exchanges. The AdMatter DNS is hosted on a Sambreel server.
AdMatter calls out to service.amasvc.com—which points to an IP which is in a range assigned to Sambreel Services, LLC—to request an ad tag. This leads to a tag being included whereby the ad slot can be sold through one of a range of major display ad networks and display ad exchanges.
When the ad slot is passed on to the major ad networks and display ad exchanges, YouTube is listed as the domain on which the ad slot has been made available. Indications are that jeetyetmedia.com, pluralmediallc.com and redfordmediallc.com are being reported as supplying the ad slot rather than Sambreel. All three of these domain names are currently protected with whois privacy, but were previously registered in the name of Arie Trouw, founder of Sambreel: bit.ly/1ey50QO; bit.ly/15Xxmoq; bit.ly/17cW94o.
Each ad slot is reloaded every 120 seconds:
Video Advertisers, Beware.
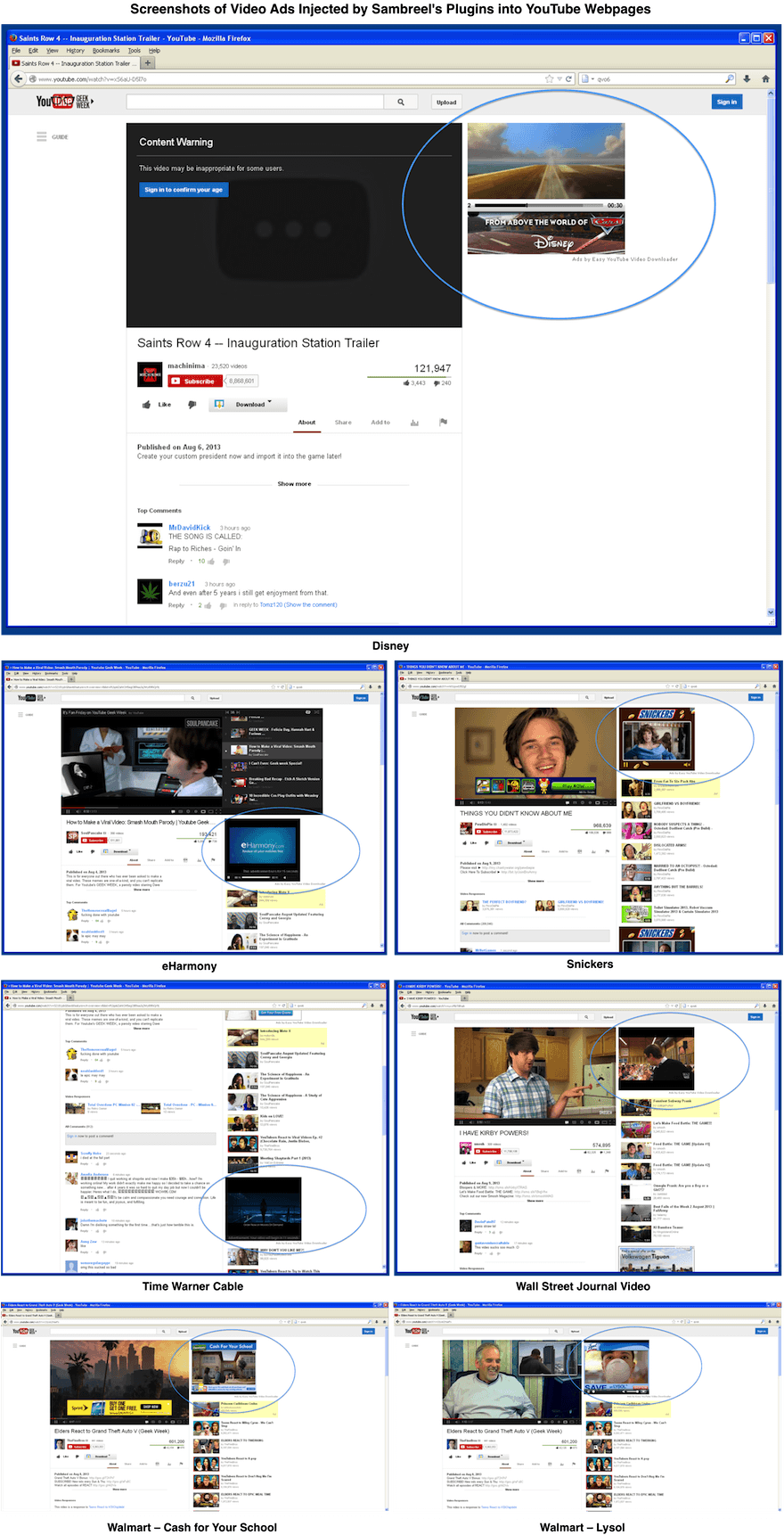
Previously, Sambreel’s adware only affected display advertisers. This is no longer the case. On some of the smaller video ad exchanges over 15% of the ad slots sold to video advertisers have been injected by Sambreel into YouTube. This happens as follows:
Video advertisers typically pay an order of magnitude more for each ad slot than display advertisers pay. Spotting the opportunity for arbitrage, some publishers have started to buy display ad slots from leading display ad exchanges. The publishers then immediately pass these purchased display ad slots on to leading video ad exchanges for sale to video advertisers—as though the ad slots are video ad slots.
Unfortunately, this rather unscrupulous form of arbitrage has meant that the ad slots injected by Sambreel adware into YouTube are now being sold to video advertisers. We measured the extent to which these Sambreel ad slots are being bought by video advertisers by analysing close to a billion video ad slots sold through non-Google video ad exchanges. We identified over 3.5 million installations of Sambreel’s YouTube-focused adware plugins. Just over 15% of the analysed video ad slots were Sambreel ad slots injected into YouTube. Example screenshots are shown below.
BACKGROUND
Defrauding Display Advertisers with Hijacked PCs
Networks of hijacked PCs are being used today to defraud display advertisers by generating billions of fake ad views. [1; 2; 3]
This type of fraud is now possible because the code underlying some of the most infamous botnets—like Zeus, Carberp and SpyEye—has been open-sourced. [4; 5; 6] Crimeware vendors have also recently started creating and selling entirely new botnet code. [7]
Two types of display advertising fraud are being committed using hijacked PCs.
The first type of display advertising fraud involves the attacker running fully automated browsers on hijacked PCs without the knowledge of the owner of the PC. These browsers visit ad-laden websites of the attacker's choosing. [8]
The second type of display advertising fraud involves hijacking the browsing sessions of the PC owners. This typically takes four forms. The owners’ clicks may be redirected to websites of the attackers choosing—where the redirect will typically be proxied via some command-and-control (C&C) server controlled by the attacker. [9] Webpages may be shown to the owners in unexpected pop-up windows. Webpages may be hidden in pop-under windows under the owners’ active browser windows. Ads may also be illegitimately injected into the webpages ordinarily visited by the PC owners. [10]
Protecting Display Advertisers from Hijacked PCs
spider.io is the only company that identifies the clusters of hijacked PCs being used to defraud display advertisers.
spider.io is a new type of anti-malware company. Whilst traditional anti-malware companies like Symantec, Sophos and Avast hunt hijacked PCs whilst having privileged access to infected machines or host networks, spider.io hunts hijacked PCs with no such privileged access. For the traditional anti-malware companies the focus is on protecting PC owners from having their machines be infected. For spider.io the focus is on preventing infected machines being used against third parties—for example, against display advertisers.
spider.io classifies the type of agent behind each individual ad request by analysing hundreds of features across the OSI layers. [11]
References
[1] "Hacked PCs Falsify Billions of Ad Clicks" – Financial Times
[2] "Who Is Behind Chameleon Botnet Tricking Marketers?" – Bloomberg TV
[3] "Botnet Steals Millions of Dollars from Advertisers" – BBC
[4] "Russian Underground 101" – Trend Micro
[5] "A Beginners Guide to Building Botnets" – ArsTechnica
[6] "A Botnet Primer for Display Advertisers" – spider.io
[7] "New Trojan #INTH3WILD: Is Cybercrime Ready to Crown a New 'KINS'?" – RSA
[8] Chameleon botnet
[9] Bamital botnet
[10] "New 'Adware' Apps Bug Facebook, Google" – Wall Street Journal
[11] "Fast Device Classification" – PCT/EP2012/055241
AdvertiserDisplayExchangeFacebookSSPVideo








Follow ExchangeWire