Now & Next: Cyber Attacks
by Hugh Williams on 13th Nov 2017 in News

The signs are innocuous: a slow network connection, a requested password update, a strange email from a colleague. The effects, however, have profound impacts on people, businesses, and governments alike. ExchangeWire’s Now & Next explores the methods and motivations behind cyber attacks, and how (or if) they can be mitigated.
Throwing your hat into the ring
Before we tar all hackers with the same brush, it is important to say that this article focuses on the threat posed by ‘black hat’ and ‘grey hat’ hackers. These groups differ from ‘white hat’ hackers, who act as security researchers – spotting vulnerabilities in organisations’ cyber security, and fixing them to protect from future, more malicious, hacks.
It is, however, the black and grey hat hackers who are doing the real damage. It is they who are responsible for the cyber attacks that affected 68% of large firms (and 66% of medium firms) in the UK in the 12 months from January 2016.
The art of the hack
Broadly speaking, malicious hackers are financially incentivised – the information they steal in breaches will be sold on the dark web to the highest bidder. To get this pay day, however, there are a number of routes open to the accomplished cyber criminal, once they have infiltrated a device:
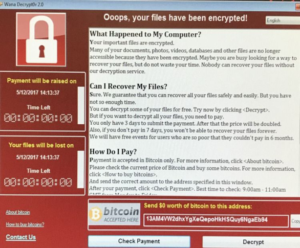
Ransoms: A form of hacking in the public eye at the moment, after ransomware known as 'WannaCry' found its way onto NHS servers. Once the computer has been infected, files are locked and users cannot access them again until they have paid the ransom, which is payable only in bitcoin. The image to the right is the same as the one seen by NHS employees when trying to access corrupted files.
Personal information sold to the highest bidder: The majority of hacks revolve around personal information (such as usernames and passwords). The 2016 hack of MySpace is a good example, with 427 million passwords put up for sale on a hacker's forum. The 2015 US Office of Personnel Management data breach, which targeted the records of four million people, and stole social security numbers, names, birthdays, and addresses, also shows how serious this type of attack can be.
Company information to the highest bidder: In this instance, hackers will be commissioned by governments or organisations looking to gain insight into the operations of a rival. The attack on Adobe in 2013, which stole source codes for Photoshop and Acrobat (allowing programmers to analyse how the software works and copy these techniques) is a good example, as is the Chinese hack targeting Google’s servers containing information about suspected spies, agents, and terrorists under surveillance by the US government.
Distributed Denial of Service (DDoS): Hackers are solicited to flood sites with more traffic than they can handle, causing them to crash. The Dyn cyberattack in 2016, which affected sites such as Amazon, Airbnb, Spotify, Netflix, and Twitter, was one of the largest attacks of this kind in history. Worryingly, it was enabled by one of the biggest opportunities in the tech space!
IoT and bitcoin are huge opportunities... for hackers!
Investment in IoT and connected technology will reach USD$547.2m (£429.01m) by 2020 – up from USD$231.9m (£181.81m) in 2014. By the same date, IoT will encompass 26 billion devices worldwide, up from 900 million in 2009. While this represents a huge opportunity for marketers, hackers are also champing at the bit here.
Despite the improvement of desktop cybersecurity, the huge rise in unprotected IoT devices means hackers now have additional devices they can target. Once added to the hacker’s botnet, these devices trigger an overload of requests to certain sites, causing them to crash. The Dyn attack is the biggest DDoS incident using IoT devices, creating its botnet from connected printers, residential gateways, surveillance cameras and baby monitors. As users neglect to change the passwords for their connected devices from factory defaults, if hackers can access these, they can add a multitude of devices to their botnet, bolstering the power of any DDoS attack.
Another exciting innovation – bitcoin – is also being exploited by hackers. The crypto-currency allows people to pay each other without using a bank or credit card company. This offers greater anonymity, with bitcoins held in virtual wallets identified by a number, rather than a name. Hackers can then transfer the bitcoin between various dummy wallets, ensuring it is untraceable, before converting it into US dollars.
Data processors
The importance of data-informed, relevant advertising has never been more important, as consumers continue to disengage with poorly targeted ads. This is leading to a demand for data processing solutions that can store the personally identifiable information (PII) required to run such campaigns. By holding and managing all this data, technology companies are painting a target on their backs for hackers looking for consumer information to sell to the highest bidder.
Halting hackers
The first step for a more cyber-safe world is for individuals to take a closer look at their cyber security habits. This involves education and training at organisational and individual levels – ensuring employees and consumers alike are aware of the need for frequent password changes, and measures such as two-step verification.
Security will have to increase at an institutional level within the next year, with the GDPR imposing fines of up to 4% of worldwide turnover for businesses neglecting the strict new data protection compliance regime. Other steps, such as raising the profiles of organisations such as Action Fraud (the fraud and cyber crime reporting centre in the UK), will also help security professionals and white hat hackers respond to, and prevent, attacks. At present, only 7% of serious data breaches in the UK are reported to Action Fraud.
Technologies such as User Behaviour Analytics (which detects potentially fraudulent activity), and Virtual Private Networks (which act as a connection between a secure server and a PC) are also available to support the fight against hackers. However, the simple truth is that there is no panacea to halt cyber attacks. There are ways to mitigate the risk of attacks; but with the rise of unsecure IoT devices and the anonymity offered by bitcoin, cyber attacks will continue to be a reality for major businesses in the future.







Follow ExchangeWire